Hey Guys,
In this blog, we will be setting a complete hacking environment using Virtual Box. In our future hacking tutorials also, we will do all of the hacking stuff on Virtual machines only(not on our primitive machine).
Need of Virtual Machines in Hacking
As a beginner in hacking, one can make several mistakes or even get infected by our own trojans. To prevent all of that stuff to mess up our primitive host machine, we will be creating Virtual Machines on Oracle Virtual Box. All of our machines will be connected via a NAT Network so that there is an unrestricted flow of network across the devices. You can even create snapshots of virtual machines and restore the original state, in case you messed the VM OS.
Setting the Environment
We will download two major virtual machines. One will be the attack machine, one will be the victim machine.
NOTE- All the attacks done on virtual machines can be done in the same way to real machines also. But never try to hack someone else's system without his concern, because it's also considered a crime.
The Victim machine will be Windows MS Edge VM & the attacking machine will be Kali Linux(Customized by Z security)

Downloading Oracle Virtual Box and required virtual machines
Refer to the link below in order to install Virtual Box and setting Windows Virtual Machine on it. king-coder.hashnode.dev/running-multiple-os..
After downloading the Windows VM, you can download Kali Linux from the link below:-
zsecurity.org/download-custom-kali
The default Username and Password is mentioned on the above website. Download Kali in the same way as you did Windows VM. Ram available to Kali should be more than that of the Windows VM because it will run a number of processes.
NOTE:- Both the Virtual Machines should be on NAT Network, otherwise they will not be able to communicate with each other.
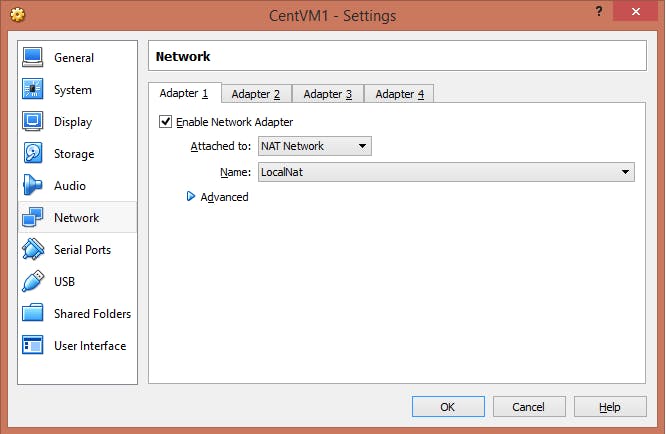
After downloading both the virtual machines, configure them according to your need. Use the login details mention in the z security website to get into Kali System.
Make sure your Kali is connected wiredly.
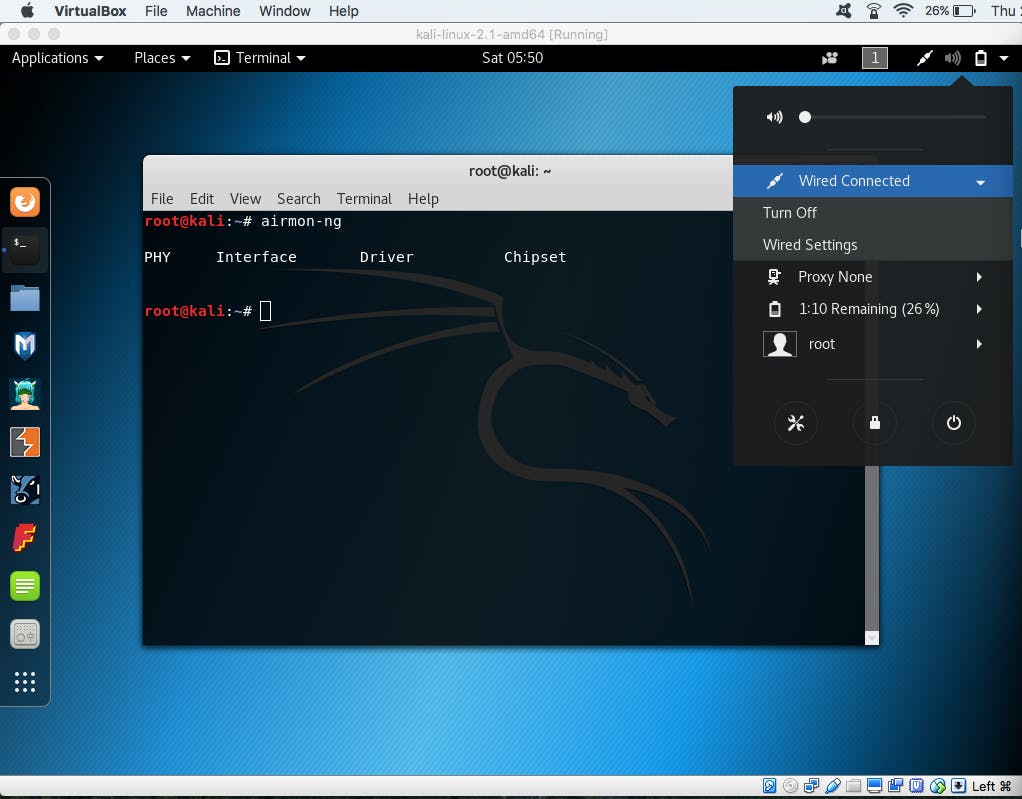
Errors you might face after downloading Kali Linux
Missing NAT Network:- youtube.com/watch?v=y0PMFg-oAEs
Black Screen Error:- zsecurity.org/got-a-blank-screen-after-impo..
After Successful opening Kali with no issue, have a look at the interface. Since we will be doing most of our work on the root terminal, let's have a look at the various commands we can use.
Link to various Linux commands:- mediacollege.com/linux/command/linux-comman..
After opening Kali our first step will be to update the system.. Run the following code in the root terminal
apt-get update
After updating, run the following code to install the terminator
apt-get install terminator
Terminator is also a root terminal with more accessibility and efficient coding features. You can spit the main window into a number of terminals using terminator
Congratulations, you just completely set up the hacking environment.
Hope you learned something new today!
Don't hesitate to comment below to raise any queries or suggestions.
Will see you guys very very soon!! :)
